AWS API Policies
Introduction
Usage of all Zadara Cloud Services-supported AWS services and actions are governed by their corresponding AWS-managed policies. These policies can be assigned per project to users, groups of users, and STS (Security Token Service) Roles. Zadara Cloud Services usage is governed by Zadara IaaS (Infrastructure as a Service) policies together with Zadara Cloud Services roles. Zadara Cloud Services supports both AWS Managed Policies and Zadara Cloud Services Managed Policies.
AWS IAM API Policies and AWS Roles Overview
The following section provides different examples in the use of policies and roles.
Policies are attached to users, groups or IAM roles only within the context of a project.
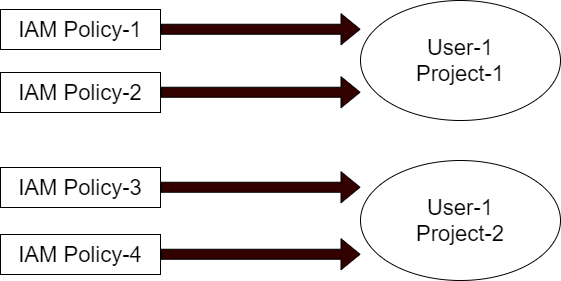
User-1 will have the permissions defined in IAM Policy 1 and IAM Policy-2 only when working within the context of Project-1. When working within the context of Project-2, User-1 will have the permissions defined in IAM Policy-3 and Policy-4.
Policies attached to users and groups within the context of the same project are aggregated.
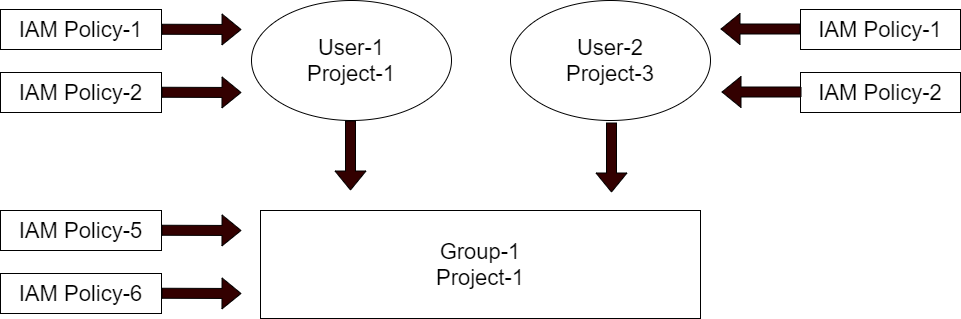
User-1 will have the permissions defined in IAM Policy-1 and IAM Policy-2 in addition to those defined in IAM Policy-5 and IAM Policy-6. On the other hand, User-2 will have the permissions defined in IAM Policy-5 and IAM Policy-6 when working within the context of Project-1. But when working within the context of Project-3, they will both have the permissions defined in IAM Policy-1 and Policy-2.
An IAM role with attached IAM policies which is added to a user, grants the user temporary credentials within the context of the IAM role’s project, once assumed.
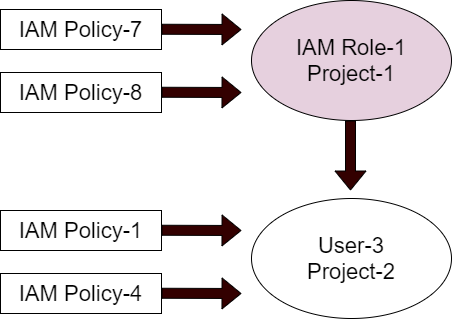
When User-3 assumes IAM Role-1, he will have the temporary permissions defined in IAM Policy-7 and IAM Policy-8, when working within the context of Project-1. When working within the context of Project-2, User-3 will have the permanent permissions defined in IAM Policy-1 and IAM Policy-4.
An IAM role with attached IAM policies which is attached to an Instance via an instance profile, grants the instance permanent credentials within the context of the IAM role’s project.
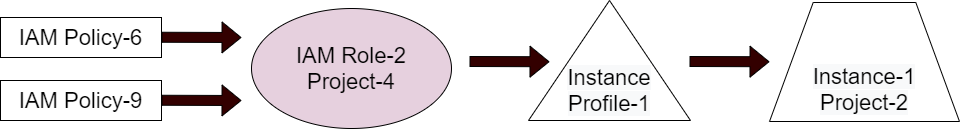
Instance-1 will have the permissions defined in Policy-6 and Policy-9, permanently, when working within the context of Project-4.
Managed AWS API Policies Supported by Zadara-IaaS
Zadara Cloud Services-managed AWS IAM API policies
Name |
Description |
|---|---|
AmazonS3BucketManagement |
Provides the ability to create buckets and read their data. |
Provides the ability to delete an EC2 AMI. |
|
Provides the ability to describe instances (including their statuses and attributes), and to create and describe images. |
|
Provides full access to all EC2 AMI actions. |
|
Provides read only access to all EC2 AMI actions. |
|
Provides read-only access to all EC2 (which includes EC2, VPC, EBS, VM Import/Export) actions, in addition to permission to start and stop EC2 instances. |
|
Provides limited access to IAM policies and full access to all other supported services. |
|
Provides the ability to obtain an IAM role using the “assume-role” action. |
|
Provides full access to all STS actions. |
ZCS-managed policy definitions
JSON policy definition examples
Examples of JSON policy definitions for ZCS managed IAM policies:
EC2AMIDeleteOnly
JSON policy definition for the EC2AMIDeleteOnly ZCS managed IAM policy:
[
{
"Action": [
"ec2:DeregisterImage"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
EC2AMIDescribeInstances
JSON policy definition for the EC2AMIDescribeInstances ZCS managed IAM policy:
[
{
"Action": [
"ec2:DescribeImageAttribute",
"ec2:DescribeImages",
"ec2:CreateImage",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
EC2AMIFullAccess
JSON policy definition for the EC2AMIFullAccess Zadara IaaS-managed IAM policy:
[
{
"Action": [
"ec2:*Tags",
"ec2:*Image*"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
EC2AMIReadOnlyAccess
JSON policy definition for the EC2AMIReadOnlyAccess ZCS managed IAM policy:
[
{
"Action": [
"ec2:Describe*Image*",
"ec2:DescribeTags"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
EC2ManageInstances
JSON policy definition for the EC2ManageInstances ZCS managed IAM policy:
[
{
"Action": [
"ec2:RebootInstances",
"ec2:Describe*",
"autoscaling:Describe*",
"ec2:StartInstances",
"ec2:DescribeTags",
"elasticloadbalancing:Describe*",
"ec2:StopInstances",
"cloudwatch:GetMetricStatistics",
"cloudwatch:Describe*",
"cloudwatch:ListMetrics"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
MemberFullAccess
JSON policy definition for the MemberFullAccess ZCS managed IAM policy:
[
{
"NotAction": [
"iam:*"
],
"Resource": [
"*"
],
"Effect": "Allow"
},
{
"Action": [
"iam:ChangePassword",
"iam:GetUser",
"iam:CreateAccessKey",
"iam:ListAccessKeys",
"iam:DeleteAccessKey"
],
"Resource": [
"arn:aws:iam::*:user/${aws:username}"
],
"Effect": "Allow"
},
{
"Action": [
"iam:GetRole",
"iam:ListAttachedRolePolicies",
"iam:ListRoles",
"iam:*InstanceProfile*",
"iam:GetPolicy",
"iam:GetPolicyVersion"
],
"Resource": [
"*"
],
"Effect": "Allow"
},
]
STSAssumeRole
JSON policy definition for the STSAssumeRole ZCS managed IAM policy:
[
{
"NotAction": [
"iam:*"
],
"Resource": [
"*"
],
"Effect": "Allow"
},
{
"Action": [
"iam:ChangePassword",
"iam:GetUser",
"iam:CreateAccessKey",
"iam:ListAccessKeys",
"iam:DeleteAccessKey"
],
"Resource": [
"arn:aws:iam::*:user/${aws:username}"
],
"Effect": "Allow"
},
{
"Action": [
"iam:GetRole",
"iam:ListAttachedRolePolicies",
"iam:ListRoles",
"iam:*InstanceProfile*",
"iam:GetPolicy",
"iam:GetPolicyVersion"
],
"Resource": [
"*"
],
"Effect": "Allow"
},
]
STSFullAccess
JSON policy definition for the STSFullAccess ZCS managed IAM policy:
[
{
"Action": [
"sts:*"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
AWS-managed IAM API policies supported by Zadara Cloud Services, with links to their JSON policy documents
Name |
Description |
|---|---|
Provides full access to AWS services and resources. |
|
Provides full access to Amazon DynamoDB via the AWS Management Console. |
|
Provides full access to Amazon DynamoDB including Export/Import using AWS Data Pipeline via the AWS Management Console. |
|
Provides read only access to Amazon DynamoDB via the AWS Management Console. |
|
Provides administrative access to Amazon ECR resources. |
|
Provides full access to Amazon EC2 Container Registry repositories, but does not allow repository deletion or policy changes. |
|
Provides read-only access to Amazon EC2 Container Registry repositories. |
|
Provides full access to Amazon EC2 via the AWS Management Console. |
|
Provides read only access to Amazon EC2 via the AWS Management Console. |
|
Provides full access to all Amazon EC2 reports via the AWS Management Console. |
|
Provides EC2 access to S3 bucket to download revision. This role is needed by the CodeDeploy agent on EC2 instances. |
|
This policy provides Kubernetes the permissions it requires to manage resources on your behalf. Kubernetes requires Ec2:CreateTags permissions to place identifying information on EC2 resources including but not limited to Instances, Security Groups, and Elastic Network Interfaces. |
|
This policy allows Amazon Elastic Container Service for Kubernetes to create and manage the necessary resources to operate EKS Clusters. |
|
Provides full access to Amazon EFS via the AWS Management Console. |
|
Provides read only access to Amazon EFS via the AWS Management Console. |
|
Default policy for the Amazon Elastic MapReduce Editors service role. |
|
Amazon Elastic MapReduce for Auto Scaling. Role to allow Auto Scaling to add and remove instances from your EMR cluster. |
|
Default policy for the Amazon Elastic MapReduce for EC2 service role. |
|
Provides full access to Amazon Elastic MapReduce and underlying services that it requires such as EC2 and S3. |
|
Provides read only access to Amazon Elastic MapReduce via the AWS Management Console. |
|
Default policy for the Amazon Elastic MapReduce service role. |
|
Allows the actions that EMR requires to terminate and delete AWS EC2 resources if the EMR Service role has lost that ability. |
|
Allows Amazon RDS to manage AWS resources on your behalf. |
|
Allows full access to use the RDS data APIs, secret store APIs for RDS database credentials, and DB console query management APIs to execute SQL statements on Aurora Serverless clusters in the AWS account. |
|
Provides access to Cloudwatch for RDS Enhanced Monitoring. |
|
Provides full access to Amazon RDS via the AWS Management Console. |
|
Amazon RDS Preview Service Role Policy. |
|
Provides read only access to Amazon RDS via the AWS Management Console. |
|
Allows Amazon RDS to manage AWS resources on your behalf. |
|
Provides full access to all Route53 Domains actions and Create Hosted Zone to allow Hosted Zone creation as part of domain registrations. |
|
Provides access to Route53 Domains list and actions. |
|
Provides full access to all Amazon Route 53 via the AWS Management Console. |
|
Provides read only access to all Amazon Route 53 via the AWS Management Console. |
|
Provides full access to all buckets via the AWS Management Console. |
|
Provides read only access to all buckets via the AWS Management Console. |
|
Provides full access to Amazon SNS via the AWS Management Console. |
|
Provides read only access to Amazon SNS via the AWS Management Console. |
|
Default policy for Amazon SNS service role. |
|
Provides full access to Amazon SQS via the AWS Management Console. |
|
Provides read only access to Amazon SQS via the AWS Management Console. |
|
Provides access to create network interfaces and attach them to cross-account resources. |
|
Provides full access to Amazon VPC via the AWS Management Console. |
|
Provides read only access to Amazon VPC via the AWS Management Console. |
|
Provides full access to Auto Scaling via the AWS Management Console. |
|
Provides read-only access to Auto Scaling via the AWS Management Console. |
|
Provides full access to Auto Scaling. |
|
Default policy for the AutoScaling Notification Access service role. |
|
Provides read-only access to Auto Scaling. |
|
Enables access to AWS Services and Resources used or managed by Auto Scaling. |
|
Policy granting permissions to AWS Auto Scaling to periodically forecast capacity and generate scheduled scaling actions for Auto Scaling groups in a scaling plan. |
|
Provides full access to AWS Certificate Manager (ACM). |
|
Provides read only access to AWS Certificate Manager (ACM). |
|
Service Linked Role Policy for AWS Elastic Load Balancing Control Plane. |
|
Enables access to AWS services and resources required for AWS KMS custom key stores. |
|
Provides access to AWS Key Management Service (KMS). |
|
Provides read-only access to CloudWatch alarms and metrics as well as EC2 metadata. Provides access to Stop, Terminate and Reboot EC2 instances. |
|
Provides full access to CloudWatch. |
|
Provides read only access to CloudWatch. |
|
Grants full access permissions to AWS services and actions required to set up and configure AWS database services. |
|
Permissions required by DynamoDB for cross-region data replication. |
|
Provides full access to Amazon ElasticLoadBalancing, and limited access to other services necessary to provide ElasticLoadBalancing features. |
|
Provides read only access to Amazon ElasticLoadBalancing and dependent services. |
|
Provides full access to IAM via the AWS Management Console. |
|
Provides read only access to IAM via the AWS Management Console. |
|
Allows an IAM user to manage their own Service Specific Credentials. |
|
Provides the ability for an IAM user to change their own password. |
|
Provides the ability for an IAM user to manage their own SSH keys. |
|
Grants full access permissions to AWS services and actions required to set up and configure AWS network resources. |
|
Provides full access to AWS services and resources, but does not allow management of Users and groups. |
|
Default policy for the Amazon RDS service role. |
|
Provides read-only access to AWS services and resources. |
|
Provides read/write access to AWS Secrets Manager via the AWS Management Console. Note: this exludes IAM actions, so combine with IAMFullAccess if rotation configuration is required. |
|
The security audit template grants access to read security configuration metadata. It is useful for software that audits the configuration of an AWS account. |
|
Grants full access permissions necessary for resources required for application and development operations. |
|
This policy grants permissions to view resources and basic metadata across all AWS services. |
Working with Managed AWS API Policies
Working with Managed AWS API Policies via the GUI
To retrieve the full list of ZCS-supported managed AWS API policies:
Navigate to the Identity & Access > AWS API Policies view.
To display the JSON policy definition of a specific managed AWS API policy:
In the Identity & Access > AWS API Policies view, click on the desired policy and select the Policy tab. The policy definition will be displayed.
To display all the users, groups and roles assigned to a specific managed AWS API policy:
In the Identity & Access > AWS API Policies view, click on the desired policy and select the Assignments tab. A list of all of the users, groups and roles assigned to this policy will be displayed.
Working with Managed AWS API Policies via the CLI
To retrieve the entire list of Zadara Cloud Services-supported managed AWS API policies:
Enter the following command:
Zadara Cloud Services @ Account-1/Project-1 > policy listThe list of all Zadara Cloud Services-supported managed policies will be displayed, together with their IDs.
To display the JSON policy definition of a specific policy:
First locate the ID of the desired policy from the list of policies with the previous command:
Zadara Cloud Services @ Account-1/Project-1 > policy listUsing the ID of the desired policy, enter the following command to get its policy definition:
Zadara Cloud Services @ Account-1/Project-1 > policy get ced7e6aca00340bd84e396c71763c7d8A variety of details about this policy including its policy definition will be displayed.
To display all of the users, groups and roles assigned to a specific policy:
First locate the ID of the desired policy from the list of policies with the previous command:
Zadara Cloud Services @ Account-1/Project-1 > policy listUsing the ID of the desired policy, enter the following command to get its policy definition:
Zadara Cloud Services @ Account-1/Project-1 > policy get-entities ced7e6aca00340bd84e396c71763c7d8All of the users, groups and roles attached to the selected policy, will be displayed.
To display all the assigned policies for all of users, groups and roles:
Enter the following command:
Zadara Cloud Services @ Account-1/Project-1 > policy assignments-listAll of the assigned policies for all users, groups and roles, will be displayed.